Prerequisites
Before adding your SSO metadata (sign-in URL) via Security in Company Settings, you need to first retrieve it from your SSO identity provider, following one of the following articles:
What is SSO?
Single Sign-on (SSO) allows Gridly users to log in to Gridly via an identity provider (IDP) of their choice. This allows admin users to better manage team access and keeps information secure.
Setting Single Sign-on in Gridly
Note
Only Owner or customized company Roles that have the same rights as Owners can access Security options. Learn more about Company Roles here.
- On the Dashboard page, click
 and select Company Settings.
and select Company Settings.
- Select Security from the side panel.
- Click Enable in the Setting Single Sign-on (SSO) section.
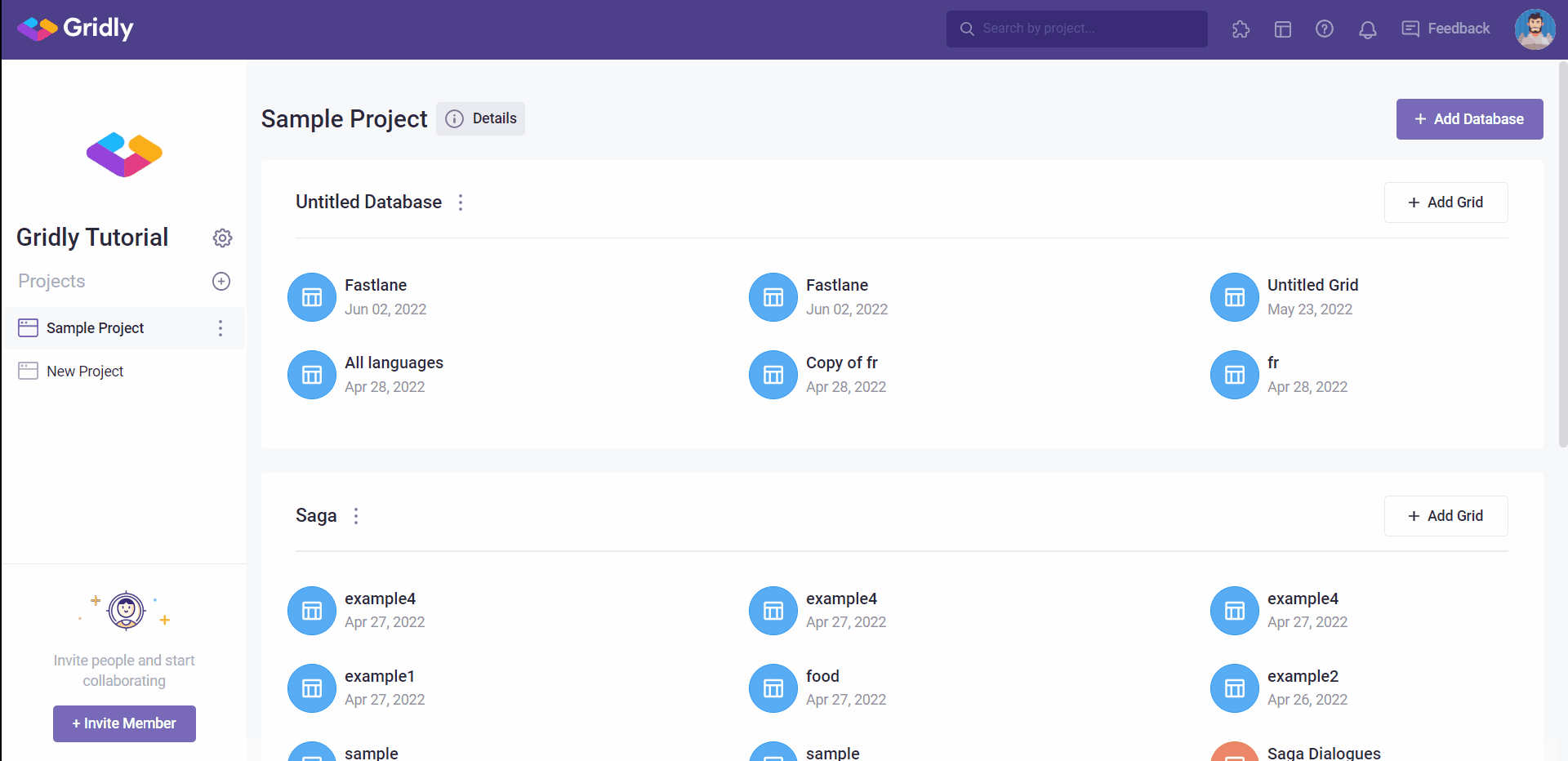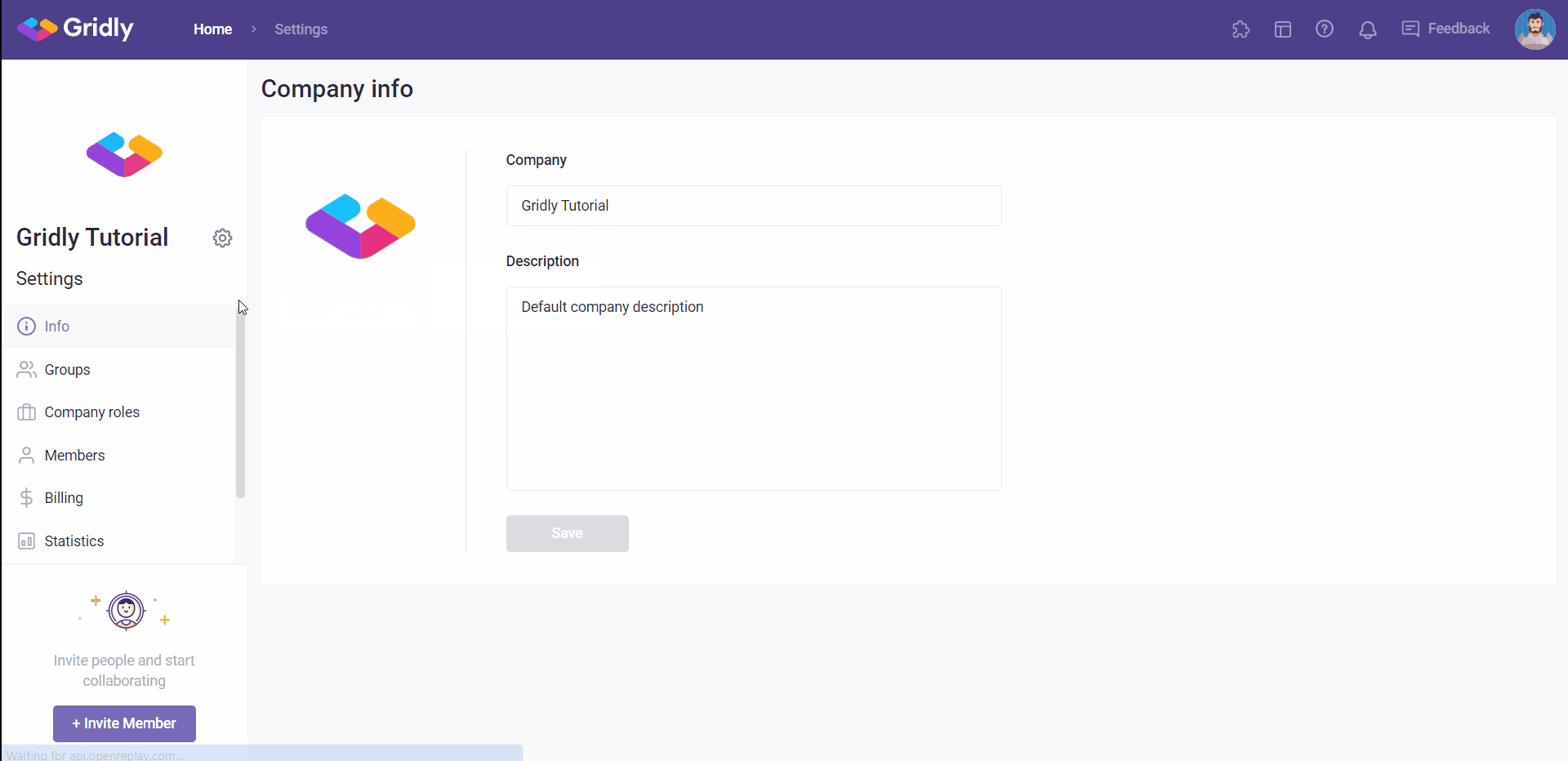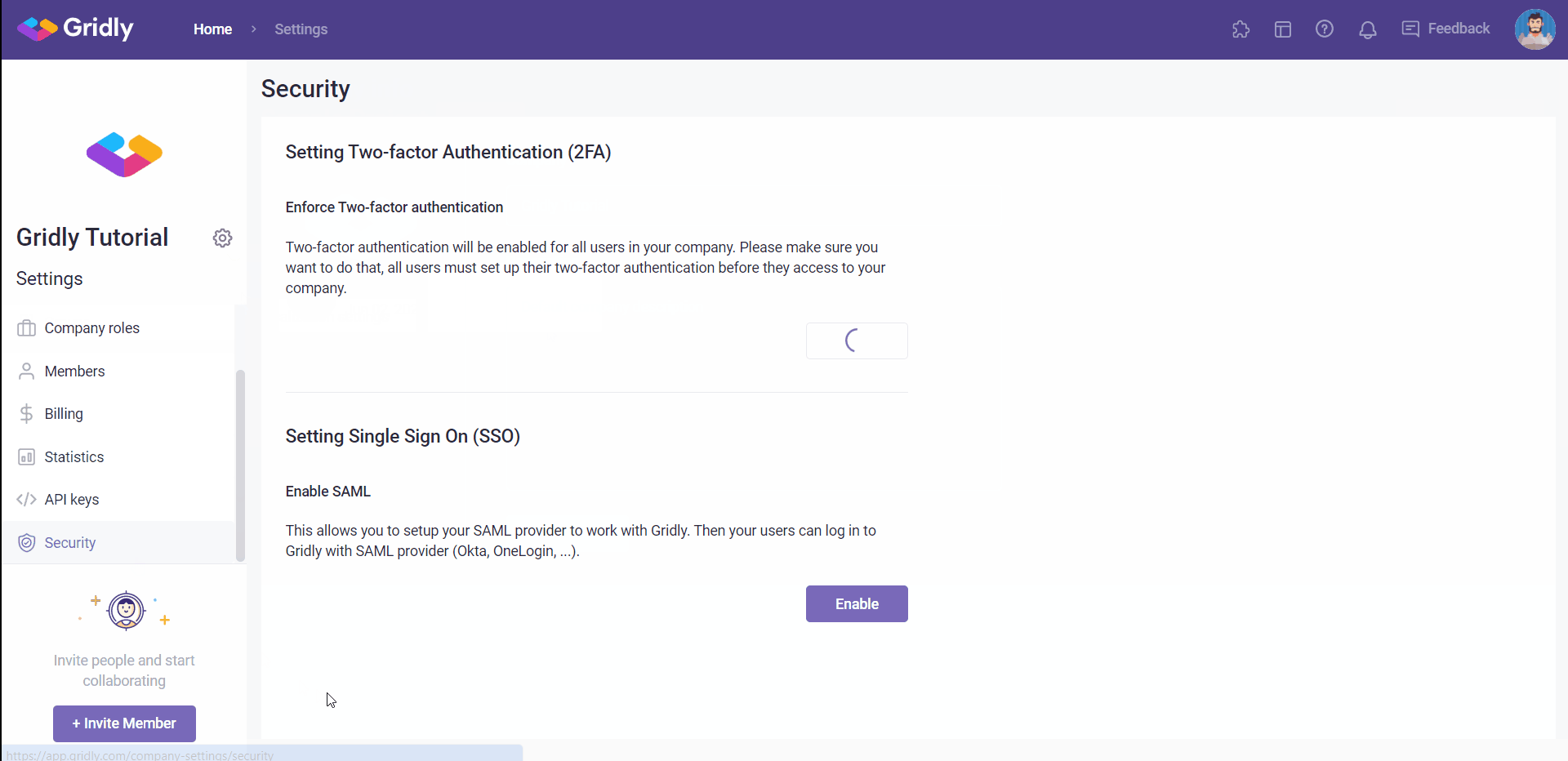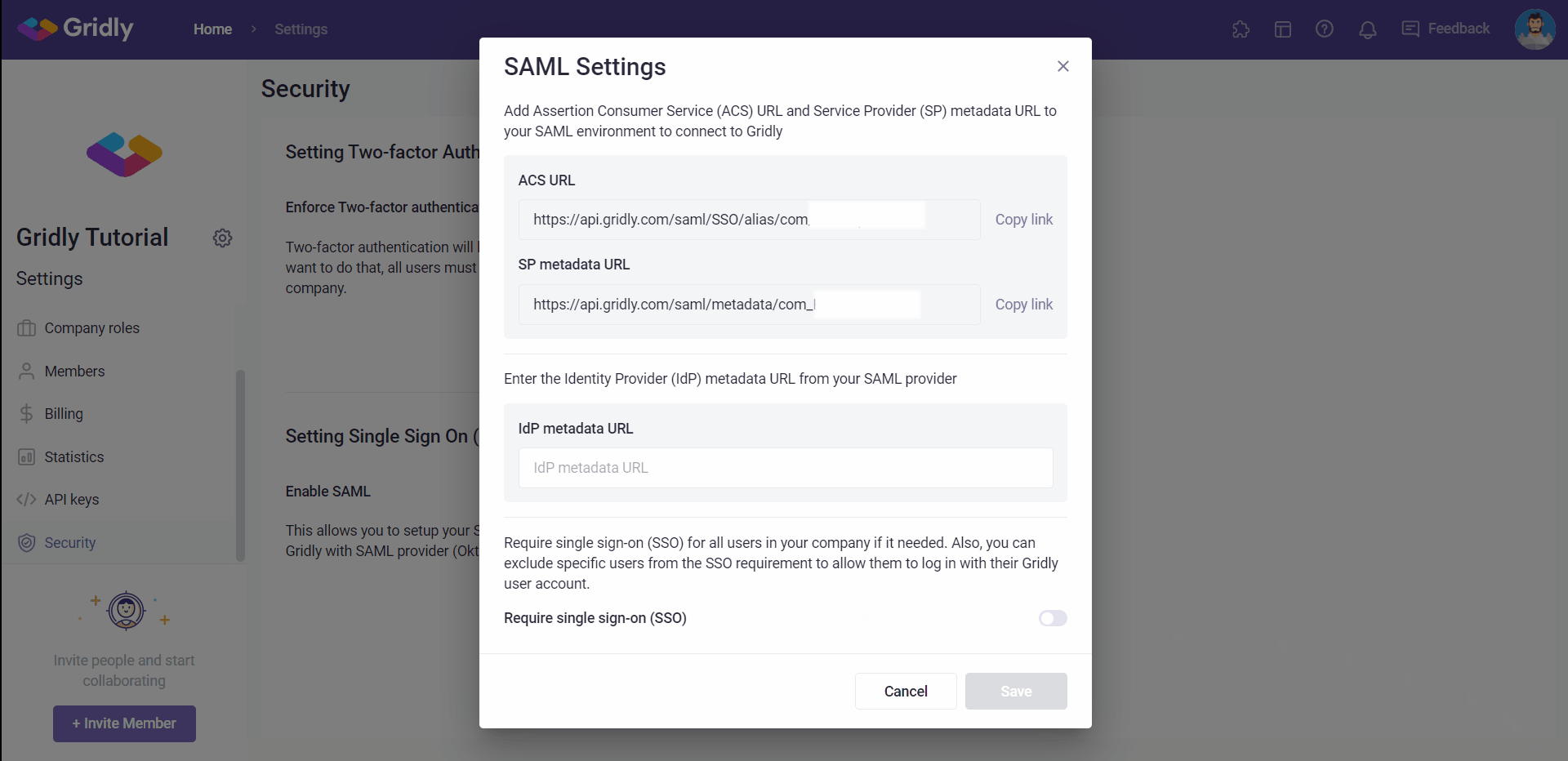
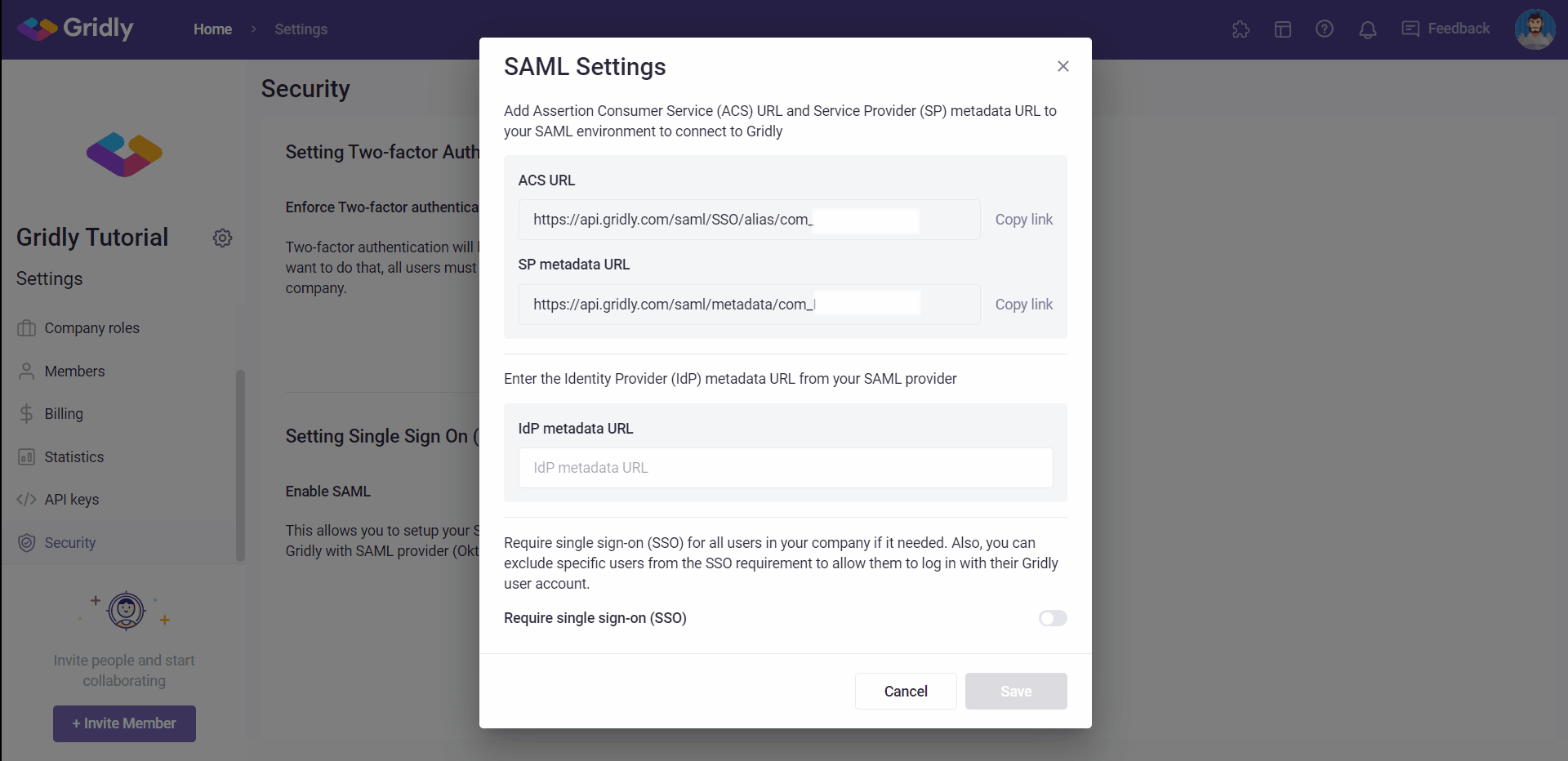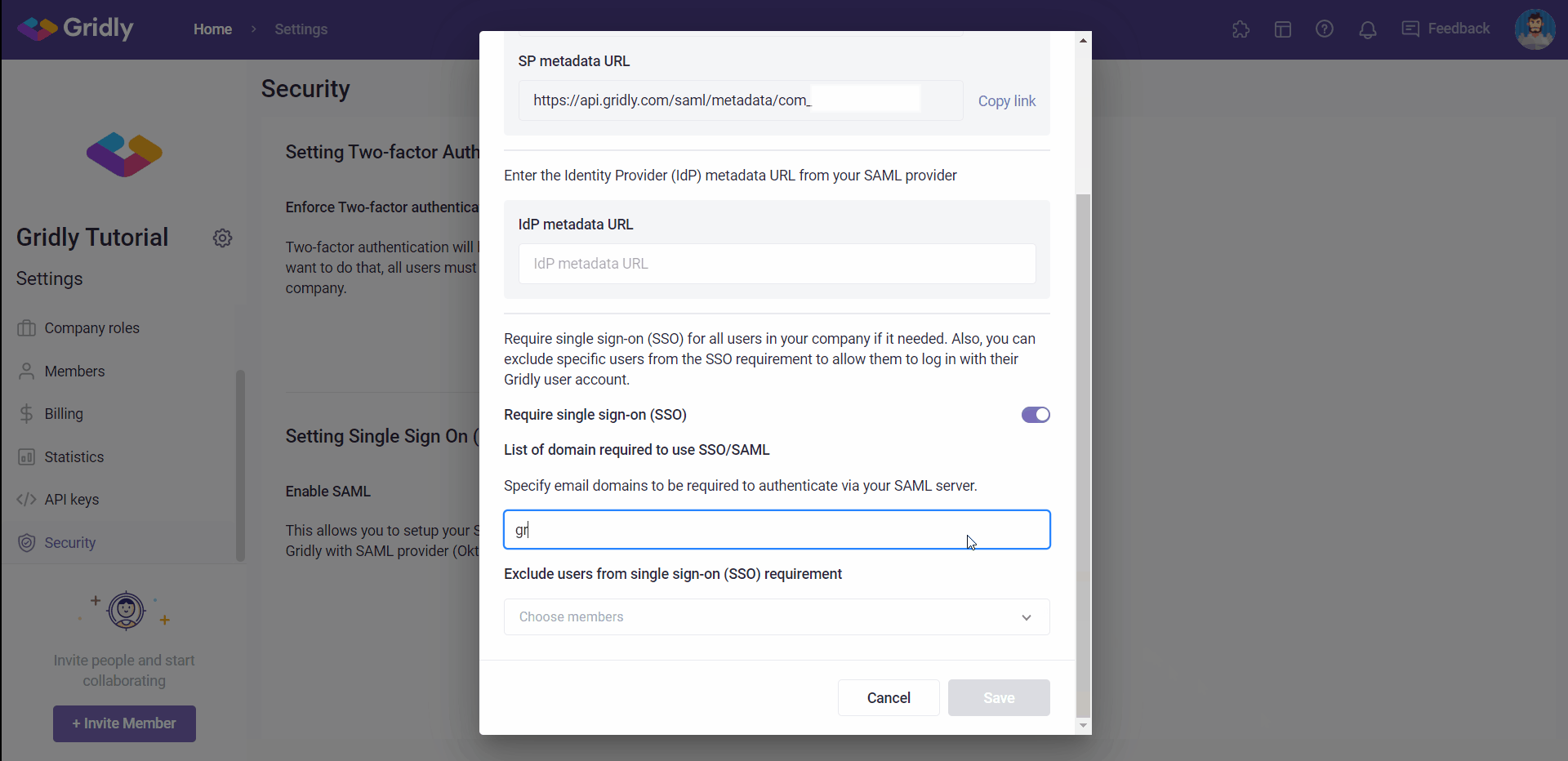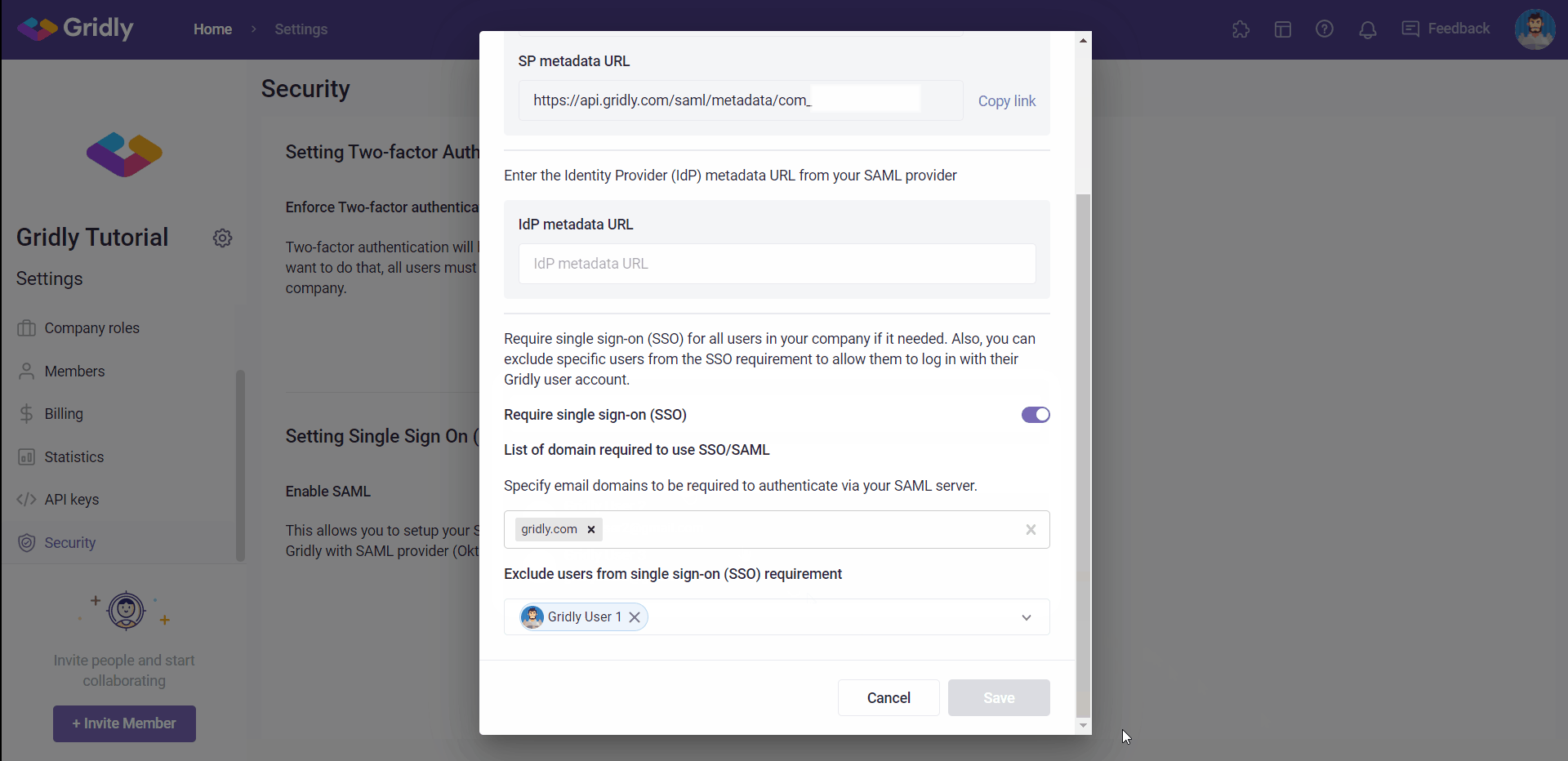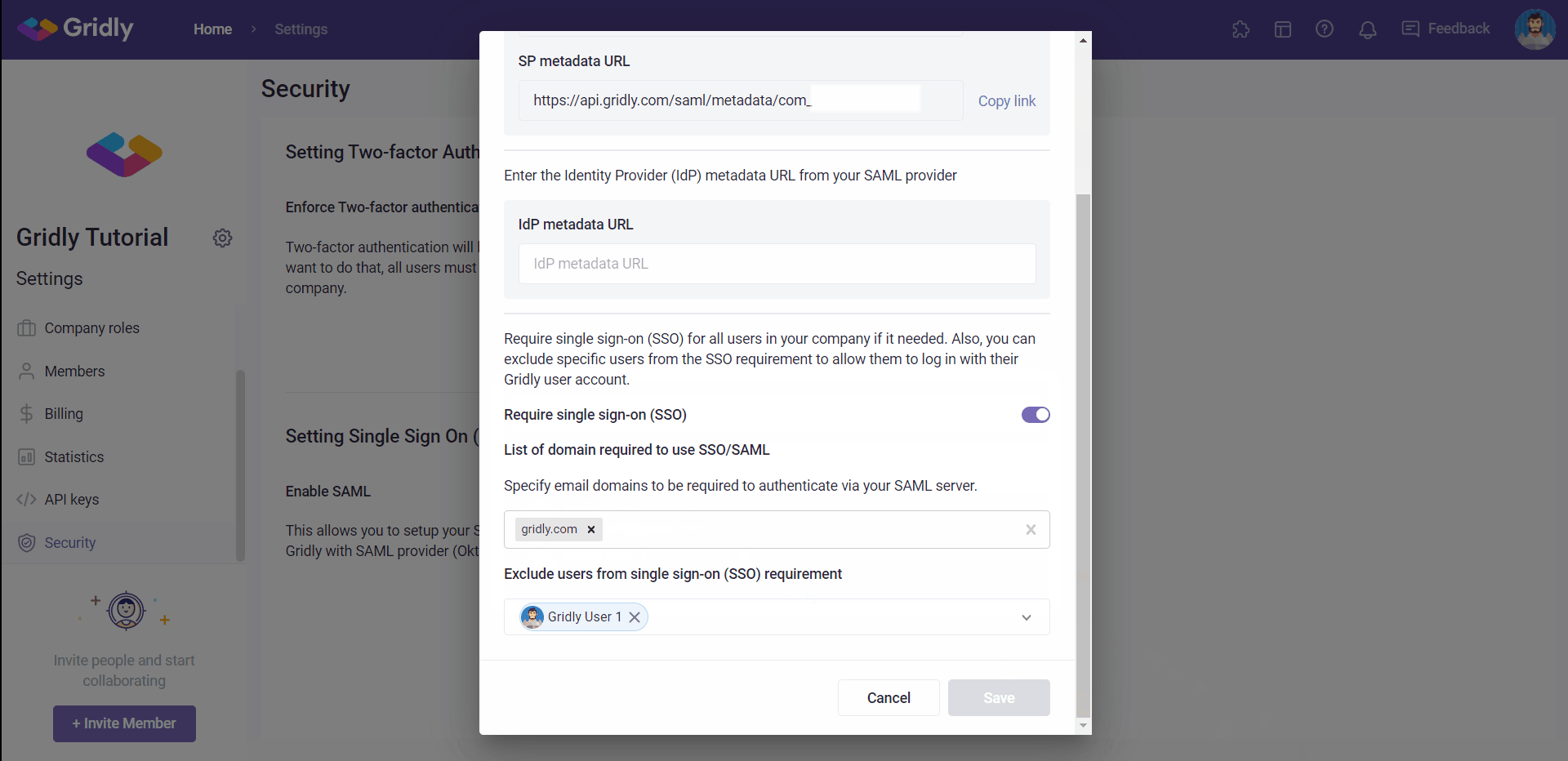
- You’ll find the Add Assertion Consumer Service (ACS) URL and Service Provider metadata URL. Copy these links and paste them to the SAML Settings in your Identity Provider application.
- Enter the IdP metadata URL that is retrieved from your SSO identity provider (following this articles if you are using Okta/ Azure).
- Click Save
Requiring Single Sign-on for all users
You can also enforce SAML SSO for your organization. When you enforce SAML SSO, all members of the organization must authenticate through your IdP to access the organization's resources.
- Open SAML Settings
- Click the toggle in Require single sign-on (SSO).
- Input the email domains that are required to authenticate via your SAML server in the textbox and press Enter .
- Exclude users from single sign-on (SSO) requirement: select members from your company that should be excluded in the SSO login and enabled login by email and password.
- Click Save to finish setting SSO in Gridly.